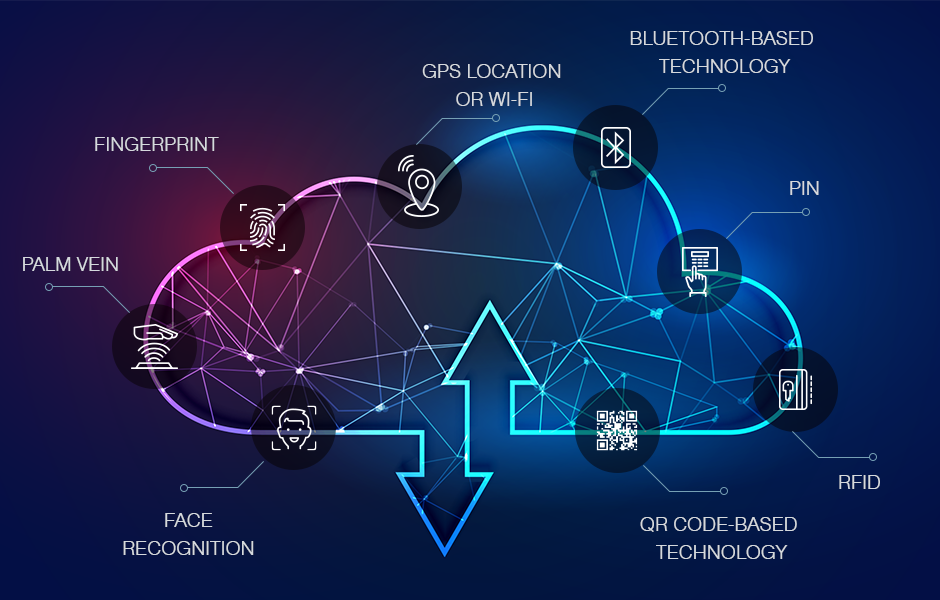
There is a growing demand for different types of user authentication technologies for physical assets, human assets, and intellectual properties. The motivation to authenticate users ranges from access control to attendance tracking of employees, visitor management system, and so on.
Organizations need to understand that PINs or passwords are not the only way to authenticate users. There is a wide range of authentication technologies and even different activities that require authentication methods. Moreover, with the type of industry, the method can vary according to the problems and demand.
What is Authentication?
Authentication is the process of identifying users that request access to a system, or a part of a system. Access control often determines user identity according to credentials such as Face Recognition, Fingerprint, PIN, Password, etc. Other authentication technologies like authentication apps, QR codes, and Bluetooth are also used to authenticate user identity. In the situation of the pandemic when the COVID has hit the world, organizations are preferring Contactless Credentials more such as Face, Palm Vein, Bluetooth, QR Code based, GPS based and RFID card. Let’s understand all of them one by one.
First of all, we will talk about contactless new age credentials.
-
Face Recognition
Facial recognition is a system used in identifying individuals by comparing live capture data with the image on record for that person. The system uses what are called nodal points (endpoints) in the face to measure variables such as the depth of the eye sockets, the width or length of the nose, or the shape of the cheekbones. There are two techniques for facial recognition. One is a traditional technique and the other is a deep learning technique. In the traditional technique, the system identifies facial features by extracting nodal features from an image of the user’s face. Then it is used for analyzing the relative position, size, and/or shape of nose, cheek, eyes, and jaw. Then these features are used to match with stored images. Whereas in deep learning technique, Face Recognition is based on innovative, deep learning technology, which evolves as per regular user interaction in different conditions. The technology checks the liveness of a face. The deep learning technique uses neural networks (algorithms models inspired by the human brain) to produce face encoding i.e. a digital string that describes a face. When two different images of the same person are passed as an input, it should return the same output for both images. This means that the neural network must be trained to automatically identify different features of faces and produce numbers based on that. In addition to this, Face Recognition can be worked on a user’s mobile as well with certain applications. Organizations that are thinking about advanced contactless technology should go for Face Recognition Technology.
-
Palm Vein Recognition
Palm Vein takes the reference of blood vessel pattern as an identifying factor. This technique is also more secure than face recognition, as veins are internal, so cannot be duplicated. Moreover, the palm has a more complicated, broader, and unique vascular pattern. It’s a contactless and hygienic technique that will work out even if the hands are dirty or wet.
-
RFID Technology
Let’s understand the working of RFID technology. The card responds with the signals to identify itself which were sent by the reader. Then the reader converts the radio waves returned from the tag into data. The data is sent to the information processing system (host or processing computer) for the identification process (filter, categorized, and analyze). Then the system grants or denies access to the user based on the Information received.
-
GPS Location or Wi-Fi
This is also a high tech solution for Contactless User Authentication. It allows users to mark their attendance automatically through mobile. It helps in tracking field employees movement and make the task easy for HR and admin departments to track the employees during working hours. It also helps in attendance correction issues as the task is getting done automatically. This also reduces the hardware cost and maintenance. It is done through the communication between the mobile application of the service provider and the company and the server. The communication is also secured between mobile and server.
-
QR Code-based Technology
QR Code-based access control allows users to scan the QR code and accordingly restrict the access of premises. It marks their attendance and opens the door when a user scans the QR code on their mobile phone camera in the mobile application. Employees/visitors can enter after the scan of the QR code and the user doesn’t need to touch anything but his/her mobile phone. This allows secure and encrypted communication.
-
Bluetooth-based Technology
This technology offers gesture-based identification for users. It opens the door when a user brings his/her mobile phone within the vicinity of a device. The registered mobile phone user can enter by bringing the mobile within eight meters of the device. Users don’t have to touch any scanner or reader. Simultaneous identification and verification of multiple users in less than one second are possible now with this advanced technology.
Now, let’s understand other technologies that require user touch or contact with the device (Door Controllers or Readers)
-
Fingerprint Technology
A Fingerprint pattern consists of a sequence of Ridges and Valleys. The dark line in a Fingerprint image is called a ridge (absorbs/randomly scatters the optical signal). The valleys are the areas between the ridges (protruded portion) (reflects the optical signal). The fingerprint sensor reads the pattern on the finger surface. Then the analog to digital converter converts the analog reading into the digital format. An interface module is responsible for communicating with external devices.
-
PIN
This method is the simplest, very basic, and outdated method of user authentication. But this can be used for two-phase verification or multilevel verification in the system. The PIN code is generally a 4 digit numeric password which the user needs to remember.
Authentication technology is always changing. Organizations have to move beyond PIN and think of authentication as a means of enhancing user experience. Authentication methods like biometrics eliminate the need to remember the long and complex PIN. As a result of enhanced authentication methods and technologies, organizations’ physical and human assets are being more and more secure. Get in touch with us for more information for a suitable system for your organization as per your industry type.
Share your views in the comment box below, or you can contact our experts to get the best suitable method for your organization’s needs.

